kawarthaNOW has received reports that “ransomware” computer incidents are on the rise locally.
Ransomware is malicious software (malware) that users unknowingly install on their computers; the software then prevents access to files on the computer unless the owner pays a hefty ransom to a hacker.
While large companies are often the high-value targets of ransomware, it’s becoming increasingly common to see smaller businesses and even individuals targetted. Currently, some computer users are being infected through a fake update for the Google Chrome browser that contains ransomware called CTB-Locker (also known as Critron).
Ransomeware is a type of malware known as a trojan. Trojans can do everything from capturing your keystrokes to turning your computer into a spam-emailing machine. In this case, the trojan encrypts the contents of your computer’s files and demands that you pay a ransom for a software “key” that will decrypt your files.
The CTB-Locker trojan and earlier variants called CryptoLocker and CryptoWall have been around since at least 2014.
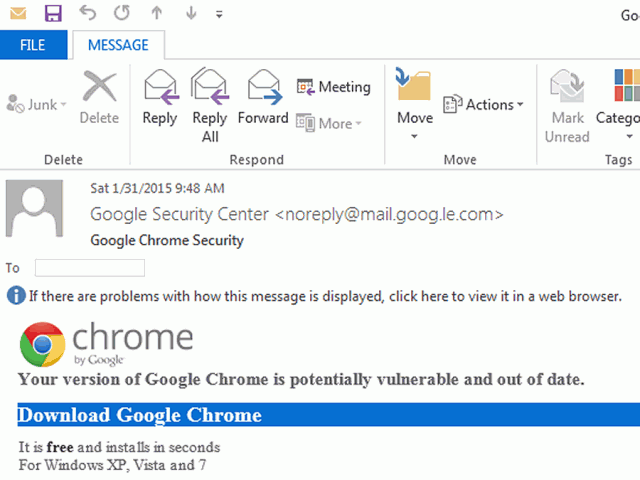
The malware isn’t attached to the email — it’s served from a link in the email. If you click on the link, you’ll be prompted to download a file called “ChromeSetup.exe” from one of various websites that have been compromised. If you run the file, you won’t be updating Chrome: you’ll be installing the trojan, which will then proceed to encrypt the contents of all the files on your computer.
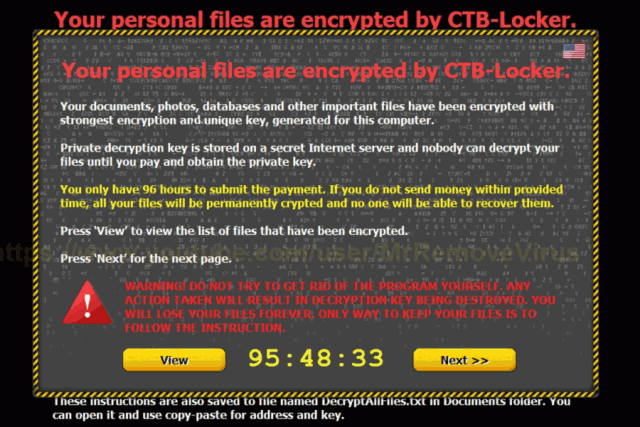
After it’s done its dirty work, the trojan displays a message on your screen demanding that you pay ransom for the key that will decrypt your files. The hackers demand payment in bitcoin, a digital currency, in an amount that is typically around $500 (the hackers use Bitcoin because it helps them retain their anonymity). The hackers give you 96 hours to pay the ransom, after which the hackers say they will destroy the decryption key and your files will be permanently encrypted.
In 2014, researchers at Dell found that the CryptoWall ransomware program infected over 600,000 computer systems in the first six months of the year, holding 5 billion files hostage and earning its creators more than $1 million.
Detroit Mayor Mike Duggan admitted that, in April 2014, one of the city’s databases was encrypted and held for a ransom of 2,000 bitcoins (worth about $800,000). In the end, the city didn’t pay the ransom because the database wasn’t needed. However, in November 2014, a county sheriff’s office in Tennessee paid a $500 ransom in bitcoin to decrypt more than 70,000 important and sensitive files.
In a recent episode of the TV series The Good Wife — whose writers always draw plotlines from recent technological trends — a legal firm’s computers get infected with ransomware.
If you do get infected by ransomware and your files are encrypted, you could choose to pay the ransom — but there’s no guarantee the hackers will send you the key so you can decrypt your files.
Although it’s impossible to decrypt your files without the key, you may be able to restore the original, unencrypted files from an operating system backup — if you have one. However, the trojan will attempt to encrypt any backups, too.
The best defense against having your computer kidnapped is prevention:
- The most important step you can take is to schedule regular back-ups of your operating system and important files onto an external hard drive. But make sure you disconnect the external hard drive from your computer after making the back-up, to prevent ransomware from accessing those files.
- Never, never, never, never click on a link directly provided in an email message, even if it appears to come from a brand or a person you know.
- Only download executable files from trusted sources.
- Keep your operating system and all your applications up to date with the latest versions and security patches. Sometimes ransomeware can be delivered through exploits in vulnerable software.
- Install anti-virus and anti-malware software (many free applications are available) and make sure to scan any downloaded files before clicking on them.
- Online (“cloud”) file services like Dropbox and Google Drive are useful for creating an off-site backup of your files, but they won’t help protect you against ransomware. As these services are “mapped” as a drive on your computer, the ransomeware can find those files and encrypt them too.
There are other more technical steps you can take to protect yourself from ransomeware. You can search for these online, or consult with a computer services company.